Detection and Prevention of DNS Tunneling Attacks: Exploring Technologies and Methodologies
Abstract
 Abstract Views: 0
Abstract Views: 0
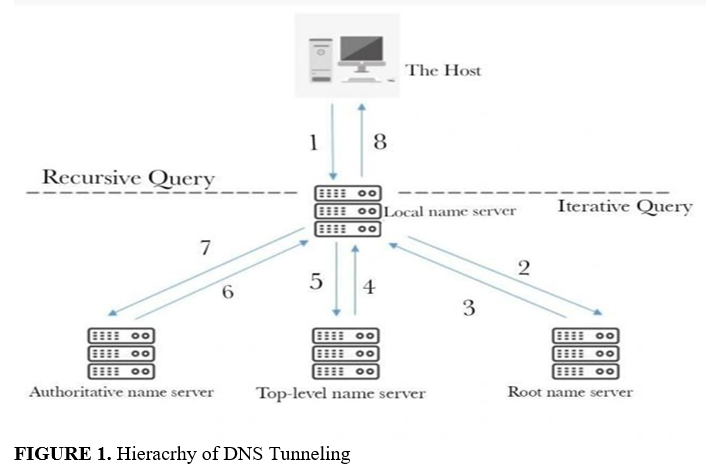
DNS tunneling attack is one of the most common and ignored attacks that the current systems are vulnerable to. This study examines the functionality of DNS in terms of DNS hierarchy and the ways through which intruder creates a tunnel. The research used both rule-based and model-based technology tools alongwith other detection-based technologies, namely signature-based and threshold-based technologies. The graphical representation of the tunnel detection technology has been shown to better understand the systematic working of DNS. Based on the review of previous research methodologies, the current research analysed methods for the detection and prevention of DNS tunneling, which includes a location-based model using GPS and observing data packet sizes.
Downloads
References
Y. Wang, A. Zhou, S. Liao, R. Zheng, R. Hu, and L. Zhang, “A comprehensive survey on DNS tunnel detection,” Comput. Net., vol. 197, Oct. 2021, doi: https://doi.org/10. 1016/j.comnet.2021.108322.
Amazon Web Services. “What is DNS?” AWS.amazon.com. https://aws.amazon.com/route53/what-is-dns/ (accessed June 01, 2022).
U. T. Gudekli and B. Ciylan, “DNS tunneling effect on DNS packet sizes,” Int. J. Comput. Sci. Mob. Comput., vol. 8, no. 1, pp. 154–162, 2019.
Sanjay, B. Rajendran, and P. Shetty, “DNS amplification DNS tunneling attacks simulation, detection and mitigation approaches,” in Proc. 5th Int. Conf. Invent. Comput. Technol., Feb. 2020, pp. 230–236. doi: https://doi.org/10.1109/ICICT48043.2020.9112413.
Elastic Security Solution. “Potential DNS tunneling via Iodine.” Elastic.co. https://www.elastic.co/guide/en/security/current/potential-dns-tunneling-via-iodine.html (accessed July 05, 2022).
S. Yassine, J. Khalife, M. Chamoun, and H. E. Ghor, “A survey of DNS tunnelling detection techniques using machine learning,” presented at the International Conference on Big Data and Cyber-Security Intelligence, Hadath, Lebanon, Dec. 13–15, 2018.
Raj. “DNScat2: application layer C&C.” Hackingarticles.in. https://www.hackingarticles.in/dnscat2-application-layer-cc/ (accessed June 02, 2022).
D. Tatang, F. Quinkert, N. Dolecki, and T. Holz, “A study of newly observed hostnames and DNS tunneling in the wild,” arXiv. Feb. 2019, http://arxiv.org/abs/1902.08454
C. J. Dietrich. “Feederbot botnet using DNS as carrier for command and control (C2).” Chrisdietri.ch. https:///post/feederbot-botnet-using-dns-command-and-control/ (accessed July 05, 2022).
ExtraHop. “DNS tunneling attack: Definition, examples, and prevention.” ExtraHop.com. https://www.extrahop.com/resources/attacks/dns-tunneling/ (accessed July 05, 2022).
M. Sammour, B. Hussin, M. F. I. Othman, M. Doheir, B. AlShaikhdeeb, and M. S. Talib, “DNS tunneling: A review on features,” Int. J. Eng. Technol., vol. 7, no. 3.20, p. 1–5, Sep. 2018, doi: https://doi.org/10.14419/ijet .v7i3.20.17266.
N. Abdelmajid, A. Amin, and S. A. R. Farhan, “Location based model for prevention DNS spoofing,” in ACM Int. Conf. Proc. Ser., Jan. 2020, pp. 1–4, doi: https://doi.org/10.1145 /3424311.3424329.
U. Inayat, M. F. Zia, F. Ali, S. M. Ali, H. M. A. Khan, and W. Noor, “Comprehensive review of malware detection techniques,” presented at Int. Conf. Innov. Comput., Lahore, Pakistan, Nov. 9–10, 2021, doi: https://doi.org/10.1109/ICIC53490.2021.9693072.
M. F. Zia, U. Inayat, W. Noor, V. Pangracious, and M. Benbouzid, “Locational detection of false data injection attack in smart grid based on multilabel machine learning classification methods,” presented at IEEE IAS Glob. Conf. Renew. Energy Hydro. Technol., Male, Maldives, Mar. 11–12, 2023, doi: https://doi.org/10.1109/GlobConHT56829.2023.10087717.
U. Inayat, F. Ali, H. M. A. Khan, S. M. Ali, K. Ilyas, and H. Habib, “Wireless sensor networks: Security, threats, and solutions,” presented at Int. Conf. Innov. Comput., Lahore, Pakistan, Nov. 9–10, 2021, doi: https://doi.org/10.1109/ICIC53490.2021.9693021
Copyright (c) 2024 Usman Inayat, Reamsha Khan

This work is licensed under a Creative Commons Attribution 4.0 International License.
UMT-AIR follow an open-access publishing policy and full text of all published articles is available free, immediately upon publication of an issue. The journal’s contents are published and distributed under the terms of the Creative Commons Attribution 4.0 International (CC-BY 4.0) license. Thus, the work submitted to the journal implies that it is original, unpublished work of the authors (neither published previously nor accepted/under consideration for publication elsewhere). On acceptance of a manuscript for publication, a corresponding author on the behalf of all co-authors of the manuscript will sign and submit a completed the Copyright and Author Consent Form.